前情提要
- 购入3865U工控软路由一台,6口千兆。
- 底层ESXI;虚拟机RouterOS,负责拨号、聚合;虚拟机de_GWD,负责网关、DNS、DHCP、V2、Pi-hole去广告。
- Qiang外VPS三台,GCP、ali-SG、bwh-CN2-GIA,负载均衡。
RouterOS配置
1.准备工作
- 直通网口2-6,网口1-lan1管理。
- 查清ros里的网口顺序;电信插eth6口,修改为CT;移动插eth5口,修改为CMCC;其余eth1-4口,分别修改为lan1-4,将4口桥接,桥接接口名为bridge1。
- 给bridge1分配个ip,比如10.10.10.3,就是ros地址。
/ip address add address=10.10.10.3/24 interface=bridge1
2.建立pppoe拨号
/interface pppoe-client add name=pppoe-CT max-mtu=1480 max-mru=1480 interface=CT user=xxxxxxxxxx password=xxxxxxxxxx add-default-route=no disable=no
/interface pppoe-client add name=pppoe-CMCC max-mtu=1480 max-mru=1480 interface=CMCC user=zzzzzzzzzz password=zzzzzzzzzz add-default-route=no disable=no
3.建立DHCP服务器
/ip pool
add name=pool1 ranges=10.10.10.2-10.10.10.250
/ip dhcp-server
add name=dhcp_pool1 interface=bridge1 address-pool=pool1 disable=no
4.防火墙基础防护
/ip firewall filter
add chain=input in-interface=pppoe-CT protocol=udp dst-port=53 action=drop
add chain=input in-interface=pppoe-CT protocol=tcp dst-port=53 action=drop
add chain=input in-interface=pppoe-CMCC protocol=udp dst-port=53 action=drop
add chain=input in-interface=pppoe-CMCC protocol=tcp dst-port=53 action=drop
add chain=input connection-state=invalid action=drop comment="Drop Invalid connections"
add chain=input connection-state=established action=accept comment="Allow Established connections"
add chain=input protocol=icmp action=accept comment="Allow ICMP"
add chain=input src-address=10.10.10.0/24 action=accept in-interface=bridge1
add chain=input action=drop comment="Drop everything else"
add chain=output action=accept comment="accept everything"
add chain=forward connection-state=invalid action=drop comment="Drop Invalid connections"
add chain=forward connection-state=established action=accept comment="Allow Established connections"
add chain=forward connection-state=related action=accept comment="allow related connections"
add chain=forward protocol=tcp action=jump jump-target=tcp
add chain=forward protocol=udp action=jump jump-target=udp
add chain=forward protocol=icmp action=jump jump-target=icmp
5.建立nat伪装与端口映射
/ip firewall nat
add chain=srcnat out-interface=pppoe-CT action=masquerade
add chain=srcnat out-interface=pppoe-CMCC action=masquerade
6.PCC宽带聚合
(1)导入国内运营商ip段
下载文件 ros-dpbr-CT-CMCC.rsc,下载地址:https://raw.githubusercontent.com/jacyl4/ros-pbr-CT-CMCC/master/ros-dpbr-CT-CMCC.rsc
导入winbox的Files里
运行如下,把ip段导入ros firewall的address lists里,供下面标记时使用。(防止重复导入,前两行是删除现有的电信段与移动段)
/ip firewall address-list remove [find list="dpbr-CT"]
/ip firewall address-list remove [find list="dpbr-CMCC"]
/import ros-dpbr-CT-CMCC.rsc
(2)排除内网通讯
/ip firewall address-list
add address=10.10.10.0/24 list=local comment=local
/ip firewall mangle
add chain=prerouting src-address-list=local dst-address-list=local action=accept comment="local"
(3)v2线路标记
示例:
- 111.111.111.111是BWH ip,注释名称BWG,走电信线路
- 222.222.222.222是GCP ip,注释名称GCP,走移动线路
/ip firewall address-list
add address=111.111.111.111 list=CTv2 comment=BWG
add address=222.222.222.222 list=CMv2 comment=GCP
/ip firewall mangle
add chain=prerouting connection-mark=no-mark in-interface=bridge1 dst-address-list=CTv2 action=mark-connection new-connection-mark=CT_conn1 passthrough=yes comment=v2
add chain=prerouting connection-mark=no-mark in-interface=bridge1 dst-address-list=CMv2 action=mark-connection new-connection-mark=CMCC_conn1 passthrough=yes
(4)PCC标记
DNS traffic
/ip firewall mangle
add chain=prerouting src-address=10.10.10.0/24 protocol=udp dst-port=53 action=mark-routing new-routing-mark="DNS traffic" passthrough=no comment="DNS traffic"
add chain=prerouting src-address=10.10.10.0/24 protocol=tcp dst-port=53 action=mark-routing new-routing-mark="DNS traffic" passthrough=no
in
/ip firewall mangle
add chain=prerouting in-interface=pppoe-CT connection-mark=no-mark action=mark-connection new-connection-mark=CT_conn comment=in
add chain=prerouting in-interface=pppoe-CMCC connection-mark=no-mark action=mark-connection new-connection-mark=CMCC_conn
PCC
add chain=prerouting in-interface=bridge1 connection-mark=no-mark per-connection-classifier=both-addresses:2/0 dst-address-type=!local action=mark-connection new-connection-mark=CT_conn comment=PCC
add chain=prerouting in-interface=bridge1 connection-mark=no-mark per-connection-classifier=both-addresses:2/1 dst-address-type=!local action=mark-connection new-connection-mark=CMCC_conn
dynamic pbr
add chain=prerouting in-interface=bridge1 connection-mark=CT_conn action=mark-routing new-routing-mark=CT comment="dynamic pbr"
add chain=prerouting in-interface=bridge1 connection-mark=CMCC_conn action=mark-routing new-routing-mark=CMCC
out
add chain=output connection-mark=CT_conn action=mark-routing new-routing-mark=CT comment=out
add chain=output connection-mark=CMCC_conn action=mark-routing new-routing-mark=CMCC
7.设置路由
/ip route
add dst-address=0.0.0.0/0 gateway=pppoe-CT check-gateway=ping distance=1 routing-mark=CT
add dst-address=0.0.0.0/0 gateway=pppoe-CMCC check-gateway=ping distance=1 routing-mark=CMCC
add dst-address=0.0.0.0/0 gateway=pppoe-CT check-gateway=ping distance=1
add dst-address=0.0.0.0/0 gateway=pppoe-CMCC check-gateway=ping distance=2
de_GWD安装
- de_GWD(Debian Gateway&DNS)专注旁路,运行于debian的一个完善套件,带界面,纯粹是为了追求更高效更极速,可以说一骑绝尘。
- DNS去污染方式有别于以往各种,效率不是以往LEDE/梅林等兼容方案能比拟的。
- 需要64位,支持普通amd64平台 以及 树莓派,香橙派 等 arm64 平台。
Github项目de_GWD
1.部署
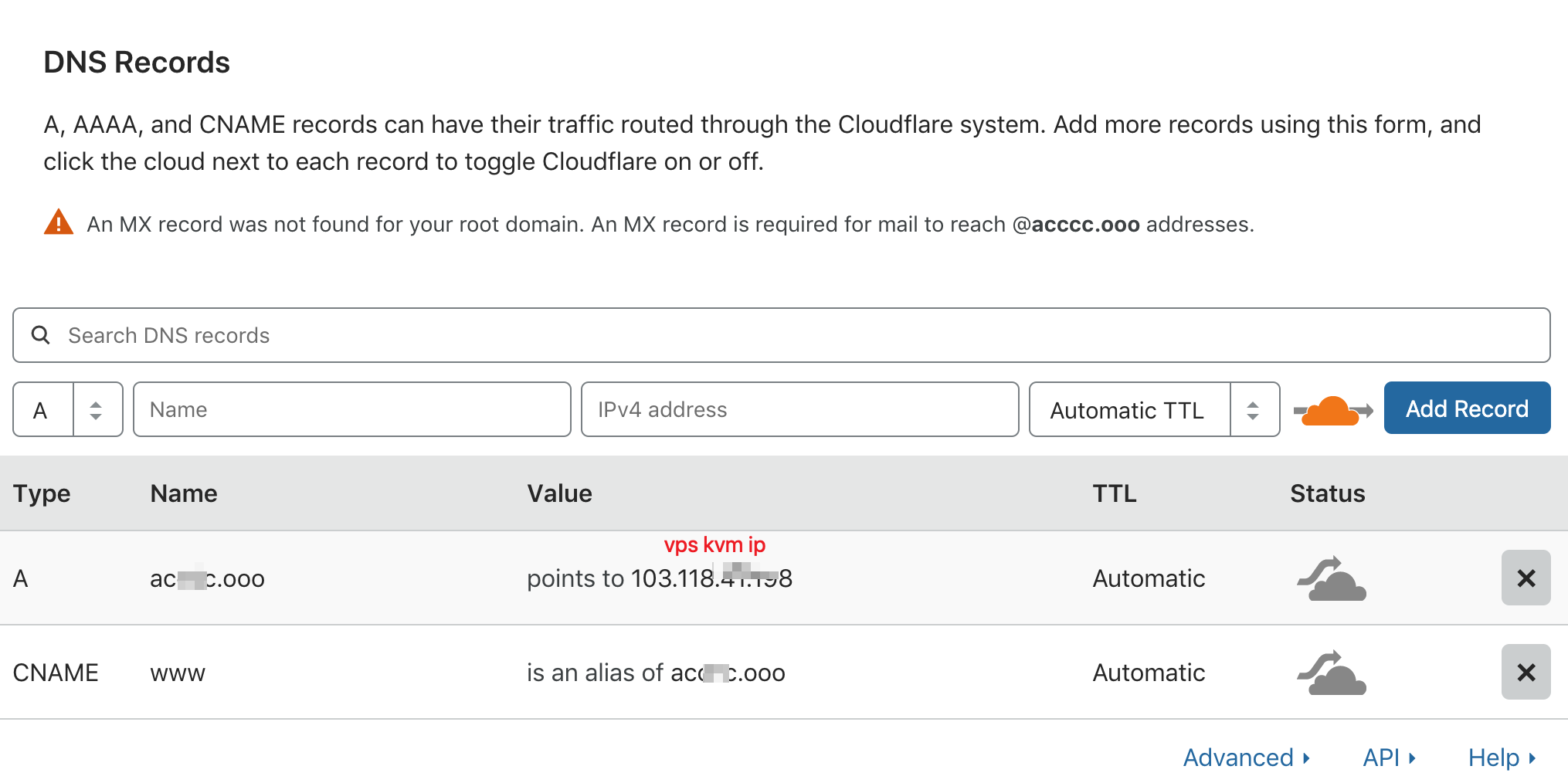
提前给自己的vps kvm 小机 准备好域名。哪怕是免费的只要能给cloudflare托管就行。二级域名不行。脚本开始安装的时候,要制作证书的。
2.服务端
apt install -y wget
bash <(wget --no-check-certificate -qO- https://raw.githubusercontent.com/jacyl4/de_GWD/master/server)
直接输出上面做好a记录的自己的域名。期间会自动生成uuid跟path。 脚本结束会打印出uuid跟path。
在线生成UUID:https://www.uuidgenerator.net
3.客户端
Compatible Edition (amd64&arm64)
apt install -y wget
bash <(wget --no-check-certificate -qO- http://xznat.seso.icu:10290/client)
General Edition (amd64)
apt install -y wget
bash <(wget --no-check-certificate -qO- http://xznat.seso.icu:10290/client_do)
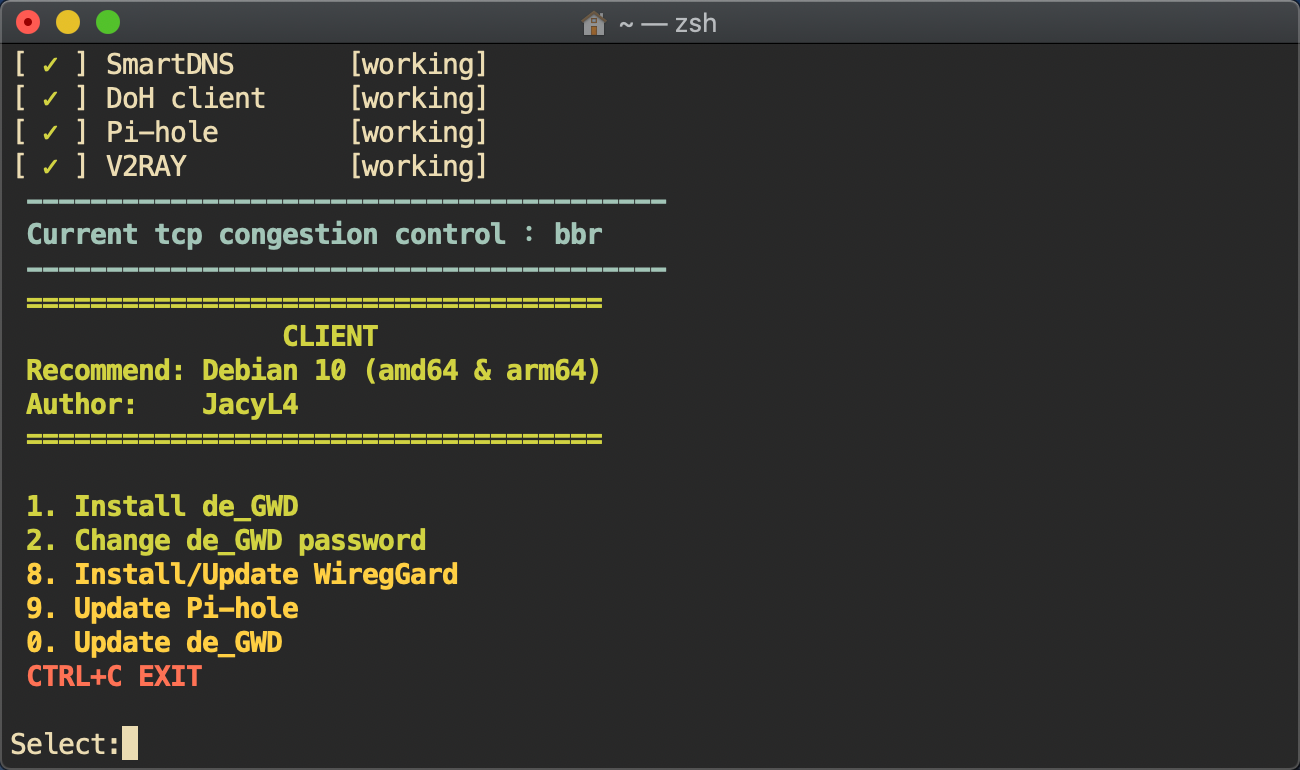
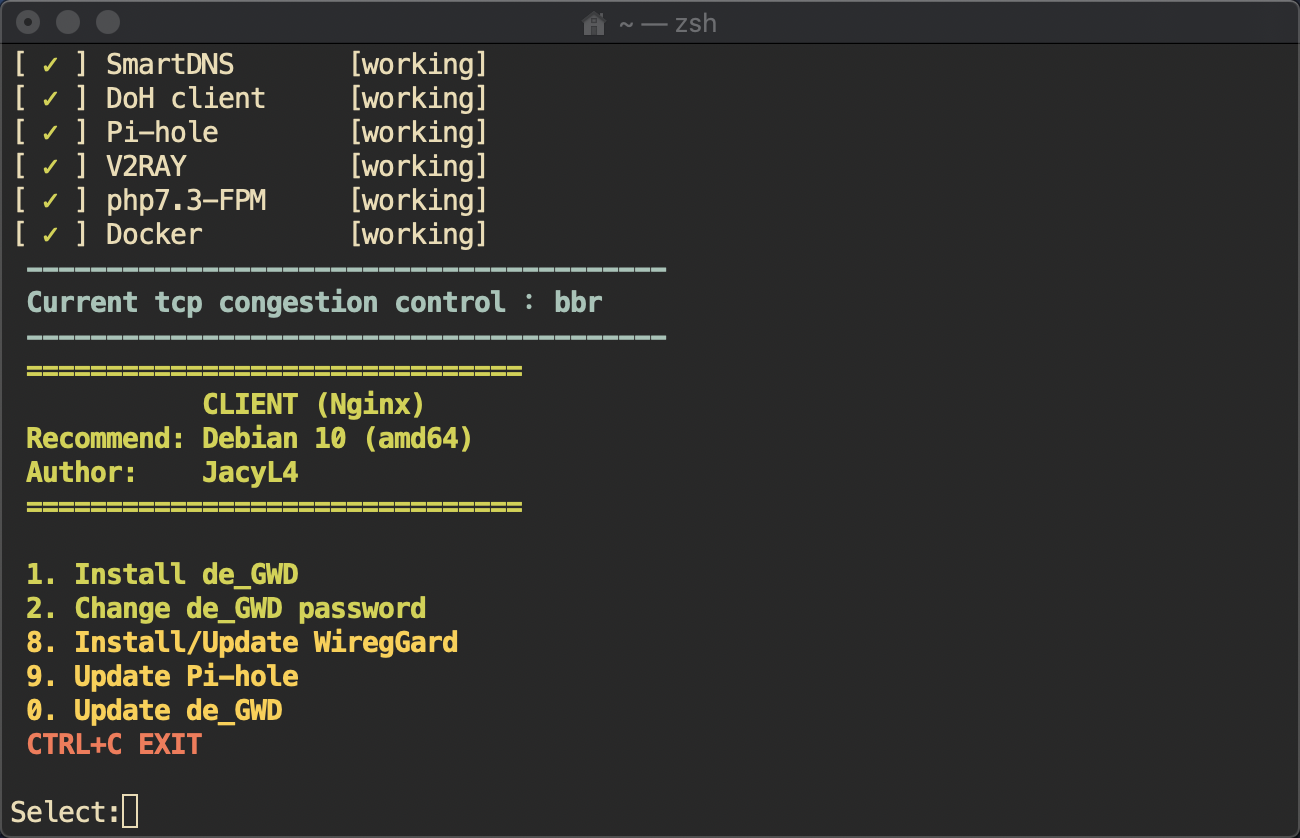
通常用第二个脚本,如果是armbian平台的话,才选第一个脚本。
首次安装前,先维持上级路由的dhcp是普通状态,确保debian能正常获取ip联网。
直接联网安装,不需要挂代理。
选项2,可以用来强制重置pihole密码。
装完后,关闭上级路由的DHCP服务,在web UI上开启de_GWD的DHCP服务。
有公网ip的话,可以选项8安装wireguard组件。
- 自动每四小时校时
- 自动每天凌晨更新分流规则